
Technology and operations professionals are familiar with IT - Information Technology - and the practices needed to keep business systems running, safe, secure and current. But many of the same approaches - and due diligence - need to be part of the assessment, long-term management care and feeding of OT (Operational Technology) when integrating automation systems.
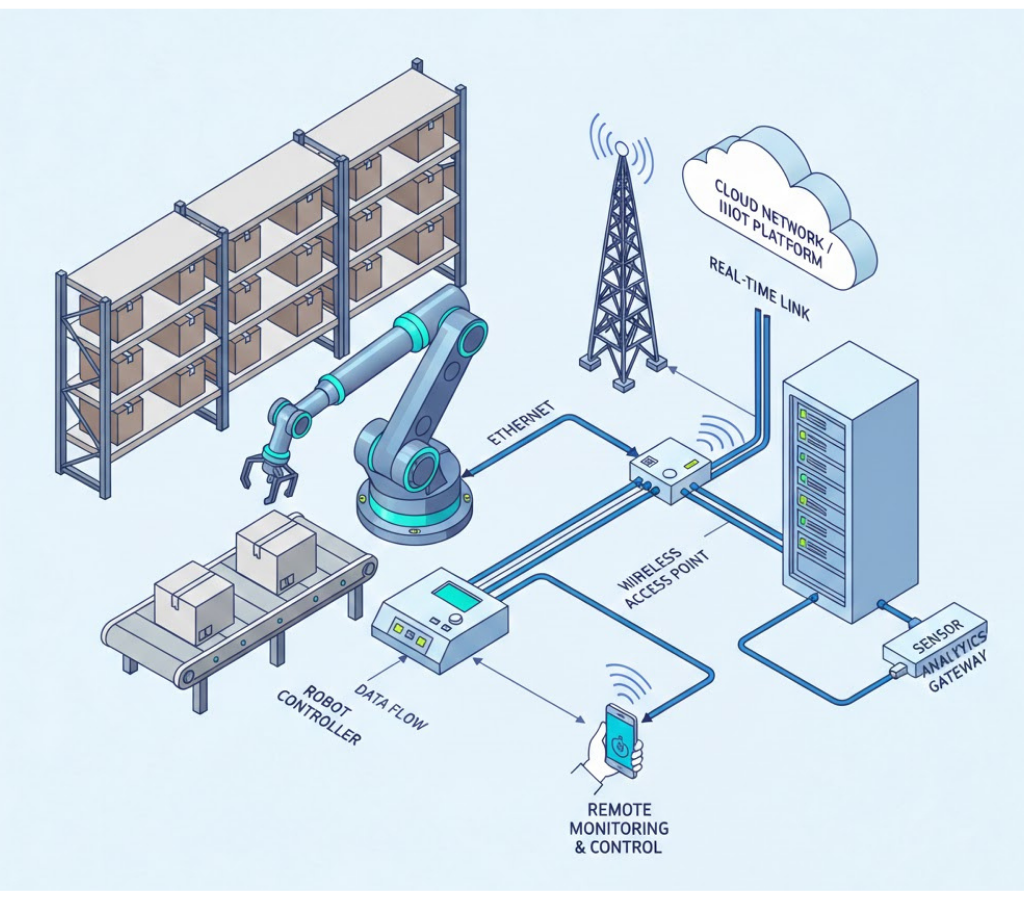
Operational technology (OT) includes the hardware and software that monitors and controls devices, processes and infrastructure in industrial settings. In the case of robotic automation, that encompasses the operating system running on the server or industrial PC, as well as the software applications required for each sensor and system component, such as the robot camera, vision AI and gripper.
Many of these systems connect to local networks and/or the cloud. Even robotic cells operating as edge computing systems require occasional connectivity for updates, and whether connectivity is persistent or occasional, the same safeguards required for any type of information technology ought to be in place to ensure adequate protection for systems, networks, data and information.
When purchasing a new robotic cell, upgrading components, or installing new or updated software, it’s important to assess the associated risks. It’s easy to assume that OT will integrate seamlessly and securely into automated operations, but like any software, there are potential hazards along the way that can trip up even the most trusted solutions. For the IT crowd, this should seem familiar.
SECURITY
Assess the security measures and vulnerabilities of the software system to protect against known and emerging threats. Evaluate and understand:
SYSTEM ARCHITECTURE
The technical architecture of the software details its design, scalability, performance and security. Review closely:
MAINTAINABILITY
Examine the code structure, architecture, documentation, and any existing bug tracking or version control systems, to see if the system is easily modified, debugged and updated. To do so:
THIRD-PARTY INTEGRATIONS
Inspect the system’s third-party integrations to gain a better understanding of which integrations are currently available and how easily more can be added, by reviewing:
COMPLIANCE
Modern systems can capture and store incredible amounts of data; if any of it is personally identifiable information (PII) it’s critical to know how the system deals with it to comply with privacy regulations such as general data protection regulation (GDPR) in the EU, California Consumer Privacy Act (CCPA) and others. Verify:
While there are many factors a company must consider when purchasing and using OT, these are some of the most overlooked. During the purchase process, if any of the systems vetted fall short in one or more of these categories, be diligent in ensuring they’re addressed before proceeding with the purchase or turning the system live.
Have questions about how Fizyr OS fares in any of these (or other) areas? We’re always here to provide answers.
.jpg)
